Using Secure Chat to Navigate Through the Pandemic’s Cyber War
An assessment and case for an alternative approach to accessible and secure corporate chat and collaboration – The MindLink Chat Engine
9 min read
Harp Gosal : Feb 9, 2022 2:30:00 PM

2021 was a record-breaking year for data breaches. According to Identity Theft Resource Center (ITRC) research, the total number of data breaches through September 30, 2021 had exceeded the total number of events in 2020 by 17%, with 1,291 significant breaches in 2021 compared to 1,108 breaches in 2020! Today, most business executives (78%) say they don’t know how or when a cybersecurity incident will affect their organizations. This level-sets the new norm for our digital world and we’ll continue to see breaches increase year on year.

Larger organizations may have a specialized department or IT security team to monitor threats but we’re seeing an increased trend where organizations are contracting external Cybersecurity Incident Response (IR) and Consulting companies for guidance on detecting, protecting and fending off potential breaches and attacks that could impact their data and networks. Specialized Cybersecurity firms usually have unparalleled access to threat intelligence from the front lines with plenty of attack research and other intelligence sources to supplement their IR teams with the latest attacker Tactics, Techniques and Procedures (TTPs). However, Cyber IR can also be managed in-house, or alternatively operate in a hybrid model combining expertise from its in-house personnel, tools and data and external specialists.
IT security teams face an ongoing challenge: how best to collect event data from every corner of their IT infrastructure and turn it into threat intelligence to prevent or stop cyber-attacks. The output from any system that processes data is only as good as the input. Thus, a formal and robust process is required. This moves us onto the Incident Response Lifecycle.
A typical Incident Response (IR) lifecycle is presented in figure 1.1. To better understand the lifecycle, we will breakdown each phase and give you a high-level illustration of the activities.
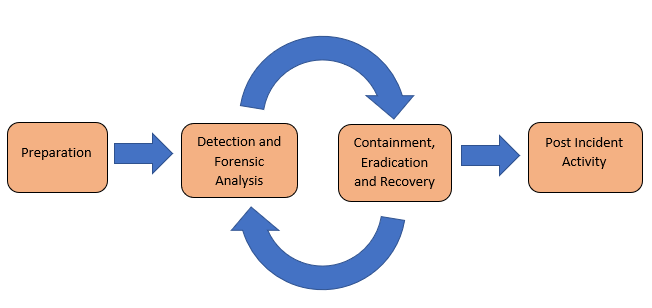
Figure 1.1 – Cybersecurity Incident Response Lifecycle
Preparation occurs when an incident has is reported by the victim and security teams, analysts and IT specialists deploy endpoints and forensic tools across a computer network and capture logs and other data telemetry.
Detection and Forensic Analysis is the phase where security analysts and consultants will analyze the data extracted from endpoints, tools, security appliances and server logs to understand the threat – the level and scale of the threat and its impact, the damage of data and property loss. This is where they attempt to understand and answer the “why” and “how”. Analysts and security consultants will observe signals, Indicators of Compromise (IOCs), threat hunt, explore detections and utilize Artificial Intelligence (A.I.) and Machine Learning to find patterns and even use a Cyber Kill Chain to microscopically trace through each stage of the attack. MITRE Attack knowledge bases may also be referenced including other sources that retain IOCs and Indicators of Attack (IOA) information to better understand the adversary and the intent of the attack.
Containment, Eradication and Recovery is the phase where analysts and IT teams will contain the threat and localize this to minimize the spread of the attack and put in processes and procedures to counter and eliminate the threat. Analysts and consultants will scour the data collected from previous phases to understand if the Tactics, Techniques and Procedures (TTPs) have been recognized at other incidents and reported or seen by other victim organizations around the globe. This gives analysts and consultants a better insight into what type of Malware or threat tool has been employed by the threat actor. This also aids in formulating the strategy to remove the threat and provide a solution for remediation and assists in setting a path for recovery. Finally, the victim will have the necessary support to reinforce its network infrastructure to prevent future attacks. In this phase, Reverse Engineering teams can often be involved to reverse engineer Malware or other tools used by the threat actor. This may happen if this type of tool or tactic has never been seen before or has had a low footprint e.g. the Malware maybe a variant of an existing Malware strain. Malware attack patterns are discovered and the mechanics of the Malware are documented and attributed to existing Malware families or if it’s a new discovery a new classification is then documented.
Post Incident Activity is where security consultants and analysts will collect data and document their findings on the case, prepare a report on the incident which will highlight the nature of the attack and remediation. The data collected from the incident is stored within a knowledge base which can be referenced to support future incidents with the hope of faster turnarounds using established detection and resolution strategies. Key data points may be shared across open source threat data and open source libraries such as Open Source Intelligence (OSINT).
Forensic Tools to facilitate the IR lifecycle, security teams which include network specialists, incident response consultants and forensic analysts have an arsenal of security tools and platforms available to them including, Security Information and Event Management (SIEM), Security Orchestration and Response (SOAR), and Extended Detection and Response (XDR) products.
SIEM supports threat detection, compliance and security incident management through the collection and analysis of security events, as well as a wide variety of other event and contextual data sources.
SOAR enables organizations to collect inputs monitored by the security operations team.
XDR is a unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.
SIEMS collect data but require a lot of manual intervention. SOAR simplifies manual remediation efforts and XDR is set to be the future by encompassing all the good from SIEMS and SOAR and automating processes to build an entirely new threat analysis and hunting ecosystem – improve threat detection and minimize response times. The collaboration between people, data and systems is very rich and complex and the aim of these tools is to break down and understand the data so that it supports the IR engagement more precisely.
The above is a very typical Security Operation (SecOps) and IR process but illustrated on a very high level and in a very simplistic manner. We have only scratched the surface and the intricacies and complexity around the entire IR and threat hunting process is beyond the scope of this article. However, it’s important to highlight the process and phases to give you some insight into how complex the discovery, detection and remediation can be after an attack has occurred.
The one thing I would like to articulate is that the process does require deep and continuous collaboration of tools, data, systems and minds – all in real-time. Every second counts and every second can cost the victim hundreds of thousands if not millions of dollars in monetary and reputation damage.
During an investigation, the collaboration process is usually highly classified and intentionally kept discrete for legitimate reasons – the victim wishes to maintain Public Relations and for the security of the case – prevent information supporting the incident falling into the wrong hands. Once an attack is discovered, threat actors usually monitor the situation the best they can to ensure their footprints are covered or to continue to cause havoc e.g. continue to threaten the victim for payment during a Ransomware attack. In this situation, I see MindLink’s tools becoming very valuable, practical and tactical tools and make a great case study to support any security and IR scenario. In the next part of this article, I will illustrate where and how MindLink’s collaboration tools can assist and support a typical Cybersecurity IR.
MindLink Anywhere is the flagship web application for instant messaging and Persistent Chat that is designed to support mission critical use cases, like our IR illustration above. MindLink Anywhere is designed to support users and engagements supporting real-time coordination and collaboration with high message volumes. Coupled with its very own MindLink Chat Engine (MCE), it supports a highly configurable, deployable and secure chat solution which support and facilitates communication and collaboration during high-stakes IR investigations which may span globally.
IR engagements require intense collaboration across security analysts, specialists, the victim and external parties irrespective of location.
MindLink Anywhere maintains a light-weight footprint and can be utilized in low network bandwidth scenarios. This is especially useful for IR consultants and analysts as they are continuously on the go and travelling across various locations and sites to collect and analyze data. It’s easy for a consultant to prepare reports and provide updates for teams and personnel even when there is a network blackout. The message simply gets sent once the network is available.
MindLink Anywhere supports real-time message translation making it a truly universal collaboration tool. It can translate any incoming private or group messages to the target language. This is extremely valuable when IR teams are coordinating with third parties or other teams around the globe.
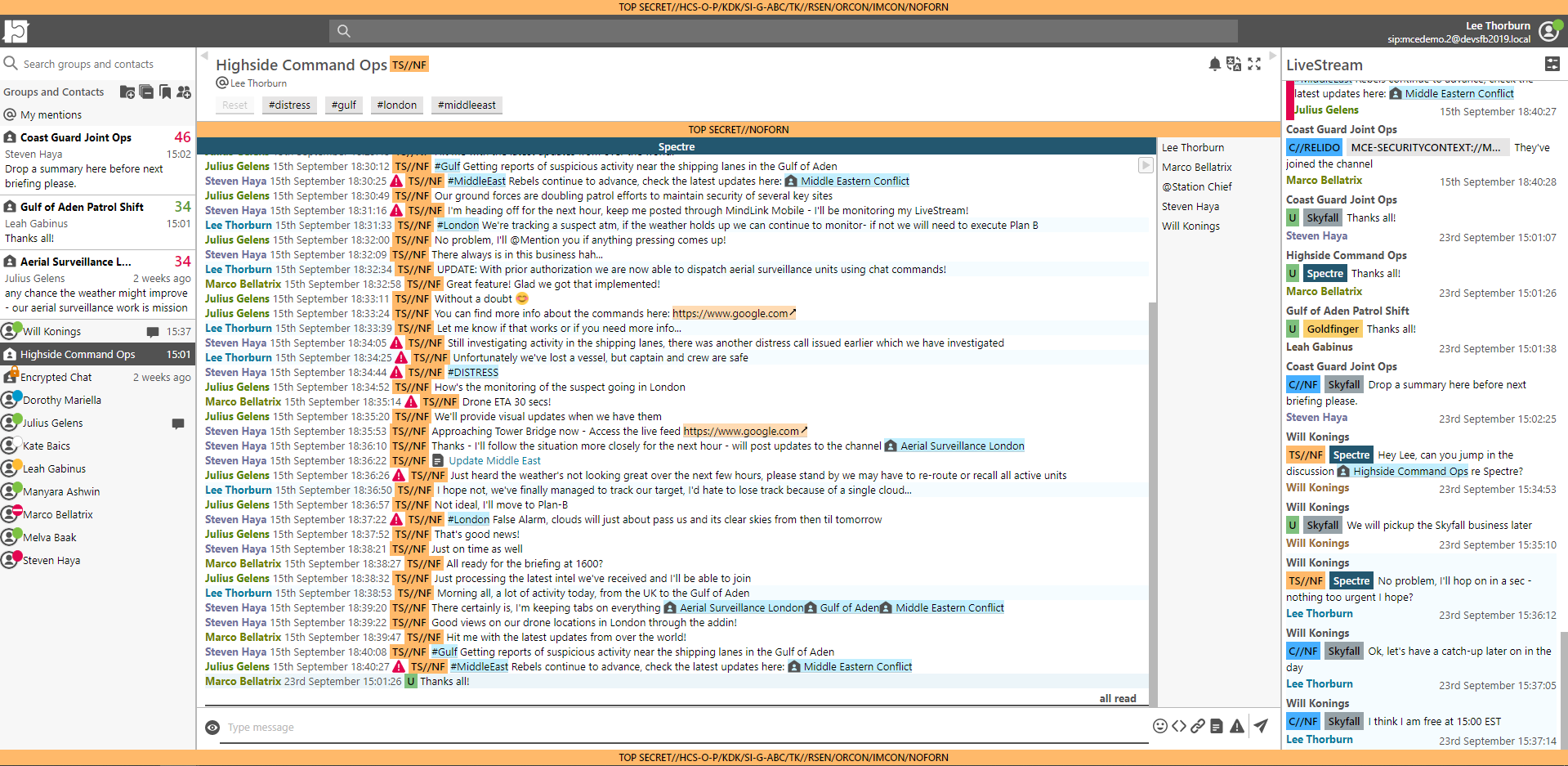
MindLink Anywhere offers an organized Workspace which is completely customizable to suit an IR mission:
MindLink support applets and add-ins. Analysts and consultants use various forensic tools and it is possible to integrate these tools inside chatrooms if a webservice api is available. XDR platforms and applications like Splunk have public APIs where you can dashboard data and this data can appear as an addin or applet inside a chatroom within MindLink Anywhere. The MindLink API can also facilitate chat content and communication across MindLink products and external third party tools. IR specialists are able to live inside their chat and have their tools available to them - all in one place.
Integrations to project management and ticketing tools such as Jira. IR consultants often create tickets to capture discoveries and observations during an investigation. These Jira tickets could be pending further investigation and at a later time. MindLink Anywhere is extensible and can easily integrate with other tools like Jira through its API. So when a Jira ticket is created by a consultant, the ticket number will appear within a chatroom or posted to specific people and parties accompanied by the link to the ticket and accompanied by other useful information. In addition, by using the MindLink API, it’s also very easy to build chatbots to relay, facilitate and govern collaboration within the MindLink Anywhere ecosystem. Rules can be baked into the chatbot to trigger on certain events e.g. Machine Learning tools may find a pattern match on an Indicator or piece of code taken from reverse engineered Malware. If the Machine Learning tool has a supported public interface, then a chatbot could easily grab the trigger from the Machine Learning A.I. tool and notify the relevant consultants of this discovery inside a chatroom.
Respondents to Accenture’s State of Cybersecurity 2021 report states that “reasons preventing the take up of the cloud revolve around security issues: about one-third of all respondents say poor governance and compliance practices around cloud security are a problem, that cloud security is too complex and that they do not have the skills internally to structure a proper cloud security framework.”1
IR engagements are not only time sensitive but also sensitive to social media gossip and to other information leaks. In context to Accenture’s statement above, MindLink Anywhere’s infrastructure supports secure private-cloud and on-premise capabilities. The chat content stays within the victim’s or IR company’s network perimeter. No risk of chat content being stored on a device or on an external cloud data array which could be prone to breaches or information leaks during transmission or storage.
Encryption and security is above key with Token based Active Directory Single Sign-on (SSO) baked into the web application. The MindLink Anywhere web application is stateless meaning that it maintains data privacy, where it does not hold message data in memory and encrypts data at REST and in transit using HTTP over TLS.
Cybersecurity organizations and specialists always seek military grade tools to assist them during an IR. Classification controls built into MindLink Anywhere can further secure communication during an IR engagement only allowing specific users to view specific messages based on classification markings. Users can select from the markings available to them when sending messages that contain classified or sensitive information. As I stated earlier, the collaboration and data exchanged between IR personnel, IR personnel to the victim and to the outside world is highly sensitive and could hinder the entire investigation if the communication or data fell into the wrong hands or appeared across social media in an un-timely manner which, could damage the victim’s reputation or intellectual property. MindLink Anywhere employs an additional level of data control especially when it comes to managing sensitive content especially during the detection and eradication phases.
The MindLink Anywhere supports all of the major browsers including Internet Explorer, Microsoft Edge, Google Chrome, Mozilla FireFox and Safari.
It integrates with cloud and on-premise chat solutions such as Microsoft Teams, Skype for Business Online, Skype for Business Online, Skype for Business 2015, 2019 (On-Premise) and its very own Chat Engine – MindLink Chat Engine (MCE) which is deployable to both on-premise or to a private cloud infrastructure.
MindLink Anywhere is packaged as a stand-alone installer for hosting in the private/public cloud and on-premise. MindLink Anywhere meets organisational requirements for uptime and scalability by deploying multiple nodes in a High Availability, Disaster Recovery or Load Balanced configuration.
IR consultants may also utilize MindLink’s Mobile application which has most of the goodness and modalities of its web counterpart. This gives analysts and consultants’ greater flexibility out in the field. The MindLink Mobile application is highly secure supporting End-to-End encryption and most of the major Mobile Application Management (MAM) solutions such as Airwatch, Mobileiron and Citrix Zen.
To conclude this article, MindLink Anywhere and the suite of MindLink products are very much aligned as tactical and mission critical collaboration tools that can support any Cybersecurity IR situation and engagement. We have only scratched the surface of the IR domain and how MindLink Anywhere can support and facilitate engagements but I hope it gives the reader a taste on how powerful MindLink is as a chat and collaboration solution for the Cybersecurity industry.
References:
1Accenture – State of Cybersecurity Resilience 2021. How aligning security and the business creates cyber resilience.

An assessment and case for an alternative approach to accessible and secure corporate chat and collaboration – The MindLink Chat Engine

“It is not enough to be joint, when conducting future operations. We must find the most effective methods for integrating and improving...

Remote working has already seen a consistent upward trend, but for the past month, remote working has become the new norm. While organisations adjust...